What is a VLAN?
A VLAN is a virtual LAN that allows you to segment your network without the need for physical segmentation logically. VLANs are very flexible and can be used to provide security, flexibility, and performance benefits. VLANs work by encapsulating Ethernet frames with a VLAN header that contains the VLAN ID. This ID is used to identify which devices are on which VLAN.
VLANs are created by adding switch ports to a particular VLAN. Devices on the same VLAN can communicate with each other without the need for a router. This makes VLANs very efficient and easy to manage. You can think of a VLAN as a virtual switch that provides isolation between devices.
VLANs are often used to separate different types of traffic such as voice, video, and data. Voice traffic is typically given priority on a network so it doesn’t experience delays or dropped packets. Video traffic is also given priority on a network so it can stream smoothly without interruptions. Data traffic is typically segregated onto its own VLAN so it doesn’t interfere with real-time traffic such as voice and video.
How does VLAN work?
A virtual LAN (VLAN) is a logical network created by switches. A VLAN contains Switch Ports that are assigned to the VLAN and has a unique identifier called a VLAN ID.
In most cases, a single physical switch can have multiple VLANs configured on it. This allows for better organization of traffic on the network and improved security as well.
When a device sends data onto the network, it includes a field called a tag that identifies which VLAN the data should be sent to. The switch looks at this tag and then forwards the data to all devices in that VLAN.
One advantage of using VLANs is that they can help reduce broadcast traffic on the network. Broadcast traffic is data that is sent to all devices on the network, regardless of whether they need it or not. By segregating devices into different VLANS, you can control which broadcasts each device receives, which can help improve performance on the network.
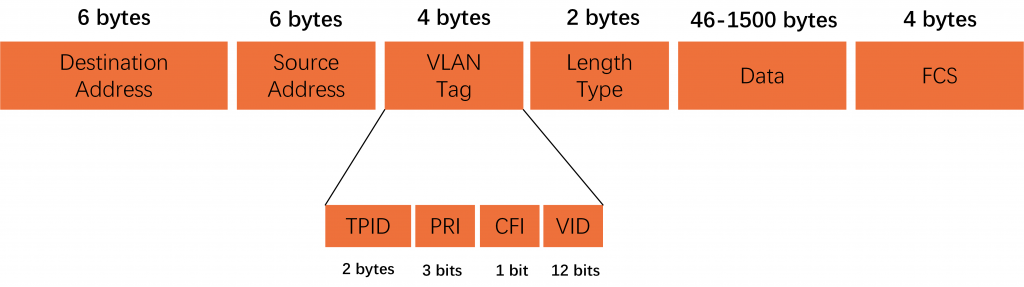
IEEE 802.1Q Frame Format
According to the information contained in its VLAN tags, a switch identifies packets from different VLANs.IEEE 802.1Q adds a 4-byte VLAN tag between the Source/Destination MAC address and Length/Type fields of an Ethernet frame to identify the VLAN to which the frame belongs.
Regular Ethernet Data Frame

VLAN Data Frame
Why would you use a VLAN?
- VLANs can be used to segment a network into smaller, more manageable sections.
- VLANs can improve security by isolating traffic and keeping it separate from other types of traffic.
- VLANs can improve performance by reducing broadcast traffic and collision domains.
- VLANs can be used to create virtual networks, which can be useful for testing or training purposes.
What is the difference between Port-based VLAN and Tag-based VLAN?
In a port-based VLAN, each port is assigned to a specific VLAN. This allows for traffic to be isolated between the different VLANs. A TAG-based VLAN uses tags to identify which packets belong to which VLAN. This allows for multiple VLANs to be assigned to a single port.
Port-based and tag-based VLANs are two different types of virtual LANs (VLAN) used in computer networking. Port-based VLAN is the most common type, where each port on a network switch is assigned to a particular VLAN. Tag-based VLAN uses special tags to identify packets that belong to different VLANs, and it is more flexible than port-based VLAN. In general, tag-based VLANS are used in enterprise networks while port-based VLANs are used in small office/home office (SOHO) networks.
VLANs are classified into the following types:
1. Data VLAN: A data VLAN is a VLAN that carries user data traffic. Data VLANS are also known as user VLANS. All switch ports that are members of a data VLAN are assigned the same VLAN ID.
2. Voice VLAN: A voice VLAN is a special type of data VLAN that is configured to carry real-time voice traffic. Voice VLANS give priority to voice traffic over other types of traffic, and all switch ports that are members of a voice VLAN are assigned the same Voice Class of Service (CoS) value.
3, Surveillance VLAN: A surveillance VLAN is a special type of data VLAN that is configured to carry real-time video traffic. Surveillance VLANS give priority to voice traffic over other types of traffic, and all switch ports that are members of a surveillance VLAN are assigned the same Voice Class of Service (CoS) value.
4. Management VLAN: A management VLAN is a special type of data VLAN that is used to carry out-of-band management traffic for devices on a network, such as switches, routers, and firewalls. Management VLANS typically use IP addresses that are not routable on the public Internet.
5. Default VLAN: A default VLAN is a network switch configuration in which all ports are assigned to a single VLAN. This can simplify switch administration by allowing all devices on the same VLAN to communicate with each other without the need for configuring separate VLANs. However, it can also create security risks by allowing unauthorized devices access to sensitive data.
6. Native VLAN: A native VLAN is a VLAN that carries untagged traffic. It is typically the default VLAN for new ports on a switch. All devices in the native VLAN can communicate with each other without tagging traffic.
VLAN Trunking
VLAN Trunking is a process of sending traffic from multiple VLANs across a single physical link. This allows for greater flexibility and efficiency when configuring network devices. In most cases, each VLAN will be assigned its own unique identifier (ID). When configuring VLAN trunking, the ID is used to specify which traffic should be sent across the trunk link.
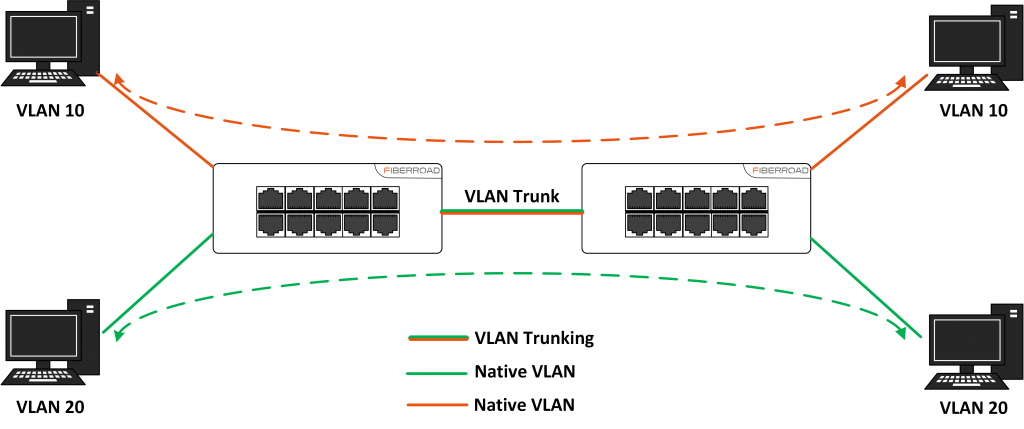
There are two main benefits to using VLAN trunking. First, it can help to improve network performance by reducing congestion on the network. Second, it can provide greater security by isolating traffic from different VLANs. This can help to prevent unauthorized access to sensitive data.
There are a few things to keep in mind when configuring VLAN trunking. First, it is important to make sure that the switch ports are configured correctly. Second, the ID of each VLAN must be unique and should not be reused on other parts of the network. Finally, it is important to test the configuration before deploying it into production.
Other Aspects of VLANs
What are Double VLANs?
A VLAN, or virtual LAN, is a group of devices on one local area network (LAN) that are configured to communicate as if they were on a separate LAN. A double VLAN is two VLANs that are configured to work together.
There are several benefits to using a double VLAN. For example, if you have sensitive data on one VLAN that you want to keep secure, you can use the second VLAN as a DMZ. This will allow you to keep the data secure while still allowing access to it from the internet. Another benefit of using a double VLAN is that it can help improve network performance. By segregating traffic into different VLANS, you can reduce congestion and improve overall throughput. Finally, using a double VLAN can increase security by providing redundancy. If one VLAN becomes compromised, the other can still provide access to critical resources.
Overall, there are many benefits to using a double VLAN configuration. If you are looking to improve security and performance, or just want more flexibility in your network design, then a double VLAN may be the right solution for you.
What is QinQ Tagging
In computer networking, QinQ tagging is a technique used to extend the capabilities of virtual Local Area Networks (VLANs). Rather than having a single VLAN per customer, QinQ allows multiple VLANs to be carried on a single physical link. This can be useful in situations where customers need to connect to multiple VLANs, or where providers need to offer different levels of service on the same physical infrastructure.
QinQ tagging was first developed by Cisco Systems, and is sometimes referred to as “Cisco Inter-Switch Link (ISL) Routing”. It is now an industry-standard protocol and is supported by most major network vendors.
To implement QinQ tagging, each customer VLAN is given a unique Service Provider Bridge Global Identifier (S-TAG). The S-TAG is used to identify the customer VLAN when it is carried over the provider network. When the customer VLAN reaches its destination, the S-TAG is removed and the original customer VLAN ID is restored.
QinQ tagging can be used in conjunction with other techniques, such as Quality of Service (QoS), to provide different levels of service to different customers. For example, a provider could give higher priority to customers who are paying for premium service levels.
Overall, QinQ tagging provides a flexible way to extend the capabilities of VLANs while still maintaining compatibility with existing network hardware and software.